How To Use Magic Briefcase and Copy Files to the Web Archive in Webroot?
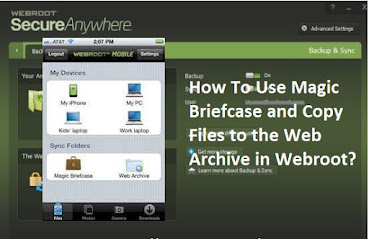
Technique to Use Magic Briefcase and Copy Files to the Web Archive: Utilize Magic Briefcase in Webroot: This essentially, a synchronized envelope which Webroot antivirus has arranged for the comfort of the client. It is there in your own Documents organizer in Windows. The records, which client keeps in the Magic Briefcase are naturally synchronized with their Webroot online record and with the other connected gadgets like PCs or cell phones. The client should utilize the Magic Briefcase to stack documents which they needed to access from different gadgets, in the event that they are voyaging or working distantly. In the event that in the event that, the clients have different gadgets which has an equivalent Webroot account, at that point they ought not load numerous records in the Magic Briefcase. f the client to utilize the Magic Briefcase, at that point they should initially open Windows Explorer and afterward select an envelope or document which you need to duplicate. After this,


